
#31: ULP Series - The ULP Stack
How the ULP stack works and why you need to understand it to ensure production quality releases. What We’ll Cover The RISC-V ULP Stack Spec ESP32 Implementation How to calculate your stack ...

How the ULP stack works and why you need to understand it to ensure production quality releases. What We’ll Cover The RISC-V ULP Stack Spec ESP32 Implementation How to calculate your stack ...

What are shared variables in the ULP realm and how to use them. What We’ll Cover What are shared variables An example of two-way shared variables How do they work Limitations of shared va...

This post covers the guts of how the ULP works and will equip you to resolve issues when they arise. What We’ll Cover What processor architecture is used How your ULP application compiled W...

Putting the main CPU in deep sleep, waking it from the ULP and properly handling the wakeup cause. Wake Up, Sleepy Head A primary reason for using the ULP in the first place is for low power appl...
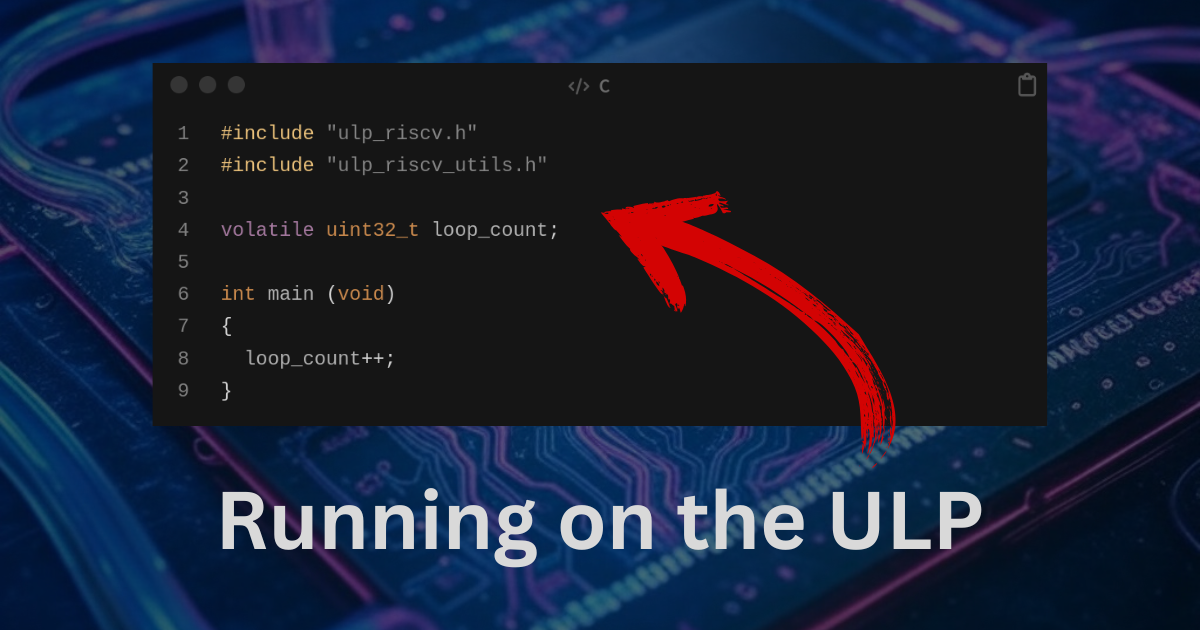
Getting Setup This repo takes a Docker-first approach and assumes you are on Linux. It can definitely work on Windows but container development is pretty cumbersome there. If you are on Windows j...
A deep dive on the nuts and bolts operation of the RISC-V ULP coprocessor on the ESP32. After running into some issues working with the ULP on the ESP32 I was inspired to crawl very deep down the ...

Espressif has released v5.3.1 as the latest stable release of IDF. The full changelog can be found here: https://github.com/espressif/esp-idf/releases/tag/v5.3.1 Notable Changes Despite being ch...
If you need to use the ESP32 as an I2C slave device please read this post first. It will save you a lot of pain and troubleshooting. If you only use the ESP32 as an I2C master, this article doe...

Previously, we covered how to achieve perfect forward secrecy guarantees in your ESP32 projects. However, even when we did that, our TLS client on the ESP32 sent cipher suites to the server that a...

The default configuration of an ESP32 project does not guarantee perfect forward secrecy(PFS) of your TLS communication. In this post we’ll cover what forward secrecy is, why you should care about ...